This article covers the following steps:
- Log in to the AWS Console
- Create an Amazon Web Services User
- Creating Access Keys for your Storage
- Configuring your Backup Settings to use your AWS bucket.
Log in to the AWS Console
Already have an Amazon Web Services (AWS) account? Sign in here.
If you don't have an AWS account yet, you will need to sign up here.
Create an IAM User
Once you have logged into the console, you will need to create a new IAM user:
Navigate to the IAM Users page in the AWS Console, click the Add users button.
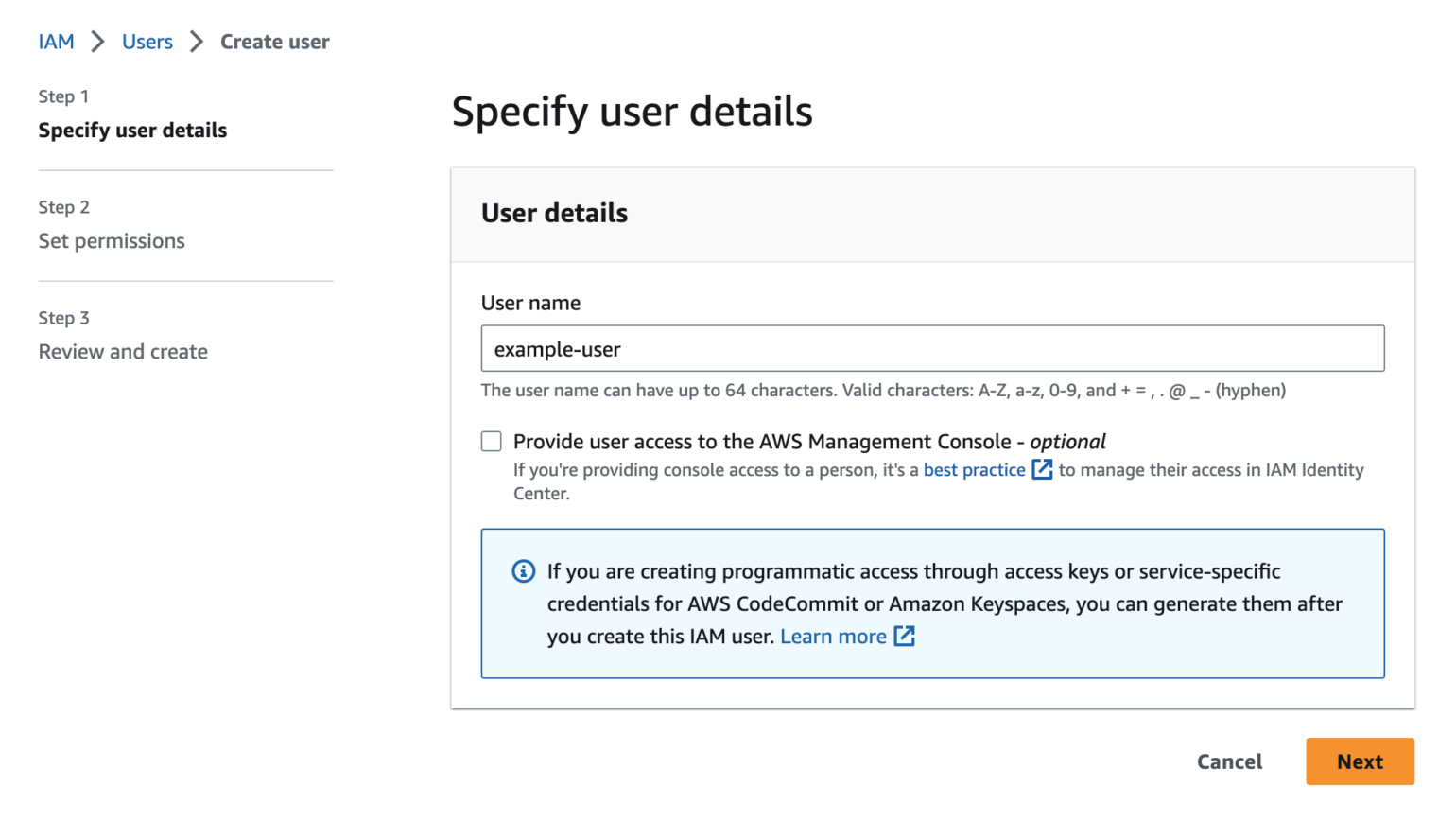
Enter a name for the user in the User name field.
Names are case insensitive and must be unique within your AWS account. User names can be a combination of up to 64 letters, digits, and these characters: plus (+), equal (=), comma (,), period (.), at sign (@), and hyphen (-).
Leave the checkbox for Provide user access to the AWS Management Console empty. Click Next to continue.
To allow the new user to manage buckets and objects in the S3 service, you need to grant it specific permissions.
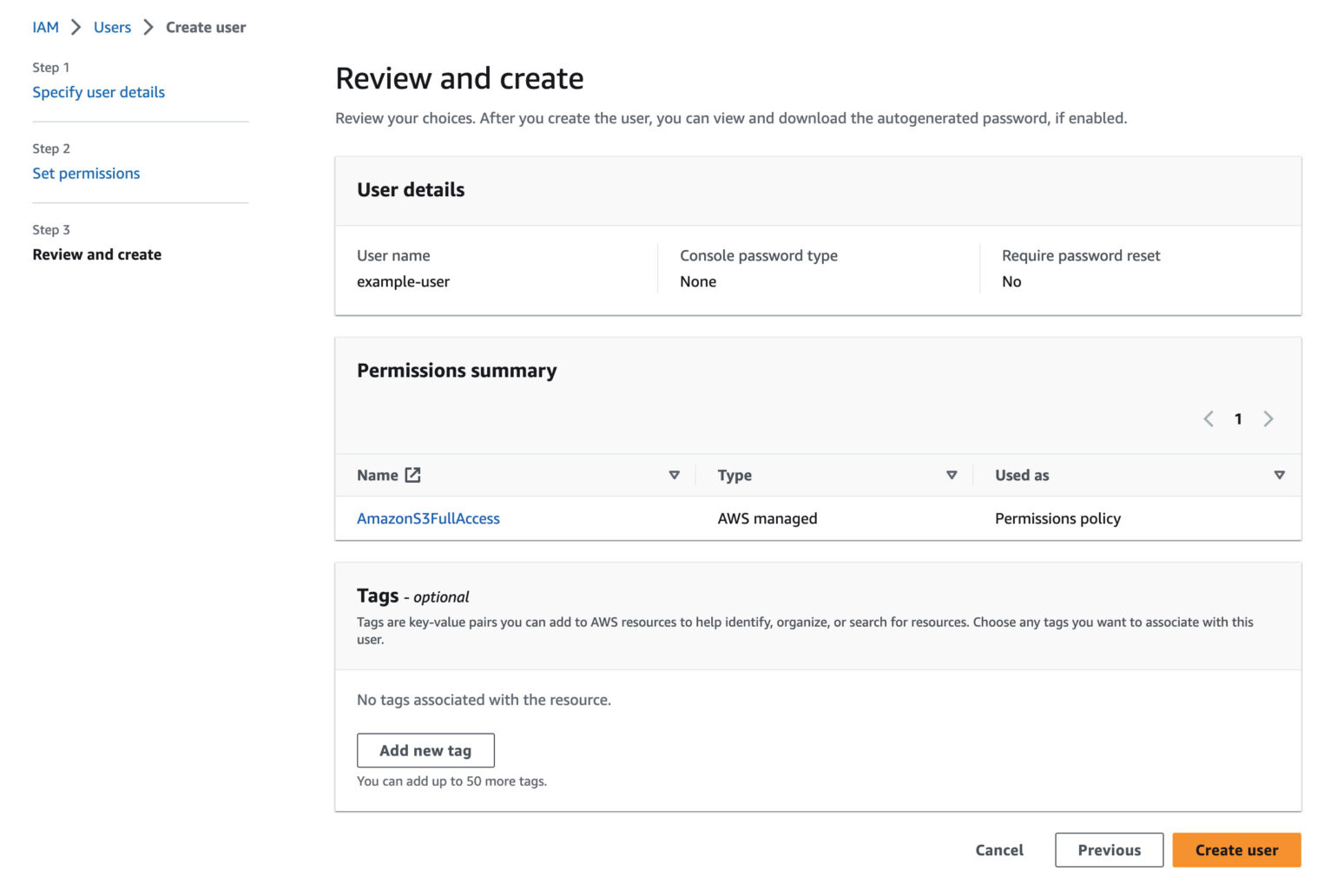
For this quick start guide we recommend giving the new IAM User full access to S3, and nothing else. Using the AmazonS3FullAccess policy helps avoid potential problems when first setting up your backup storage, but experienced users of AWS may wish to use a Custom IAM Policy. More documentation for this setup will be provided soon.
Click the Attach policies directly button, and then enter s3full in the filter policies input box.
Select the AmazonS3FullAccess policy, then click the Next button at the bottom of the page.

In the final step, you can optionally add tags before creating the new user. Adding tags is purely optional, if you're a heavy user of AWS you may have a reason to add tags here to help with management tasks.
Whether you add tags here or not, click the Create user button at the bottom of the page to go ahead and create the new user. Once done, you will be taken back to the IAM Users listing page where you will see a confirmation that the new user has been created.
Create Access Keys
Next, you need to create access keys for the new user. Click on the newly created user name in the IAM Users page in the AWS Console to open the user details page.
Go to the Security credentials tab and scroll down to the Access keys section and then click the Create access key button.
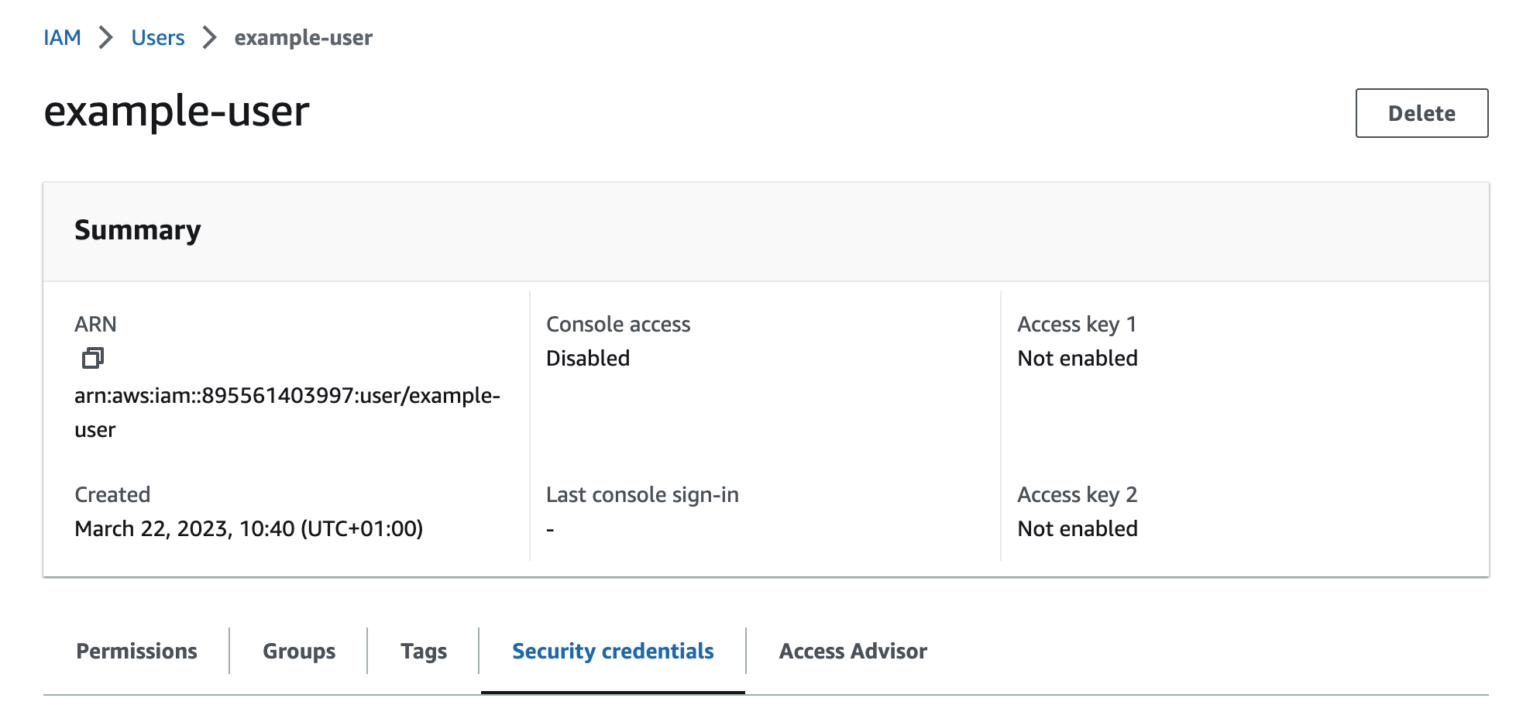

In the first step, you will be shown a list of Access key best practices & alternatives. Select Application running outside AWS and then click Next.
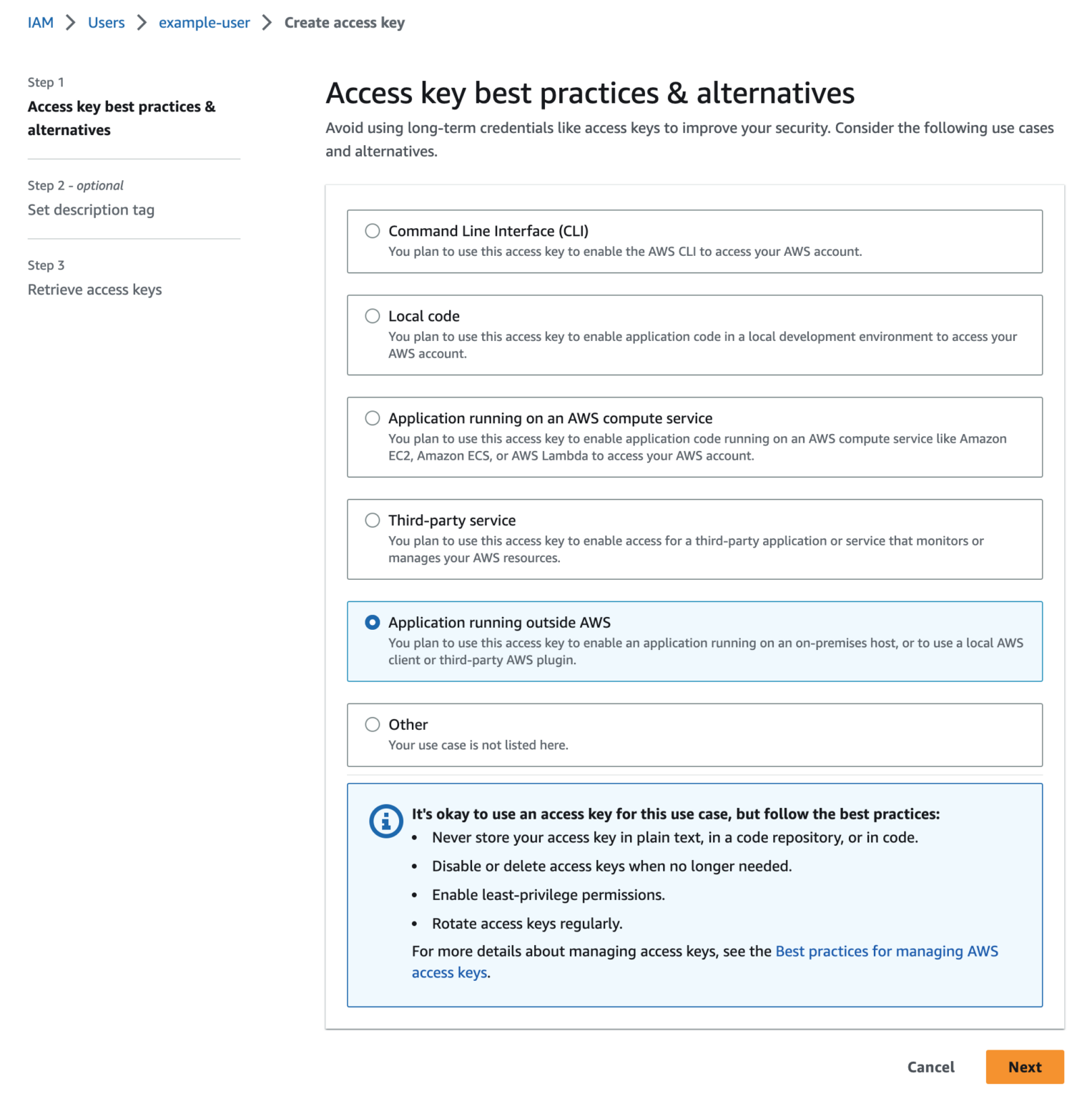
The second step allows you to set a description tag and is entirely optional, whether you add tags here or not, click the Create access key button to get to the last step.
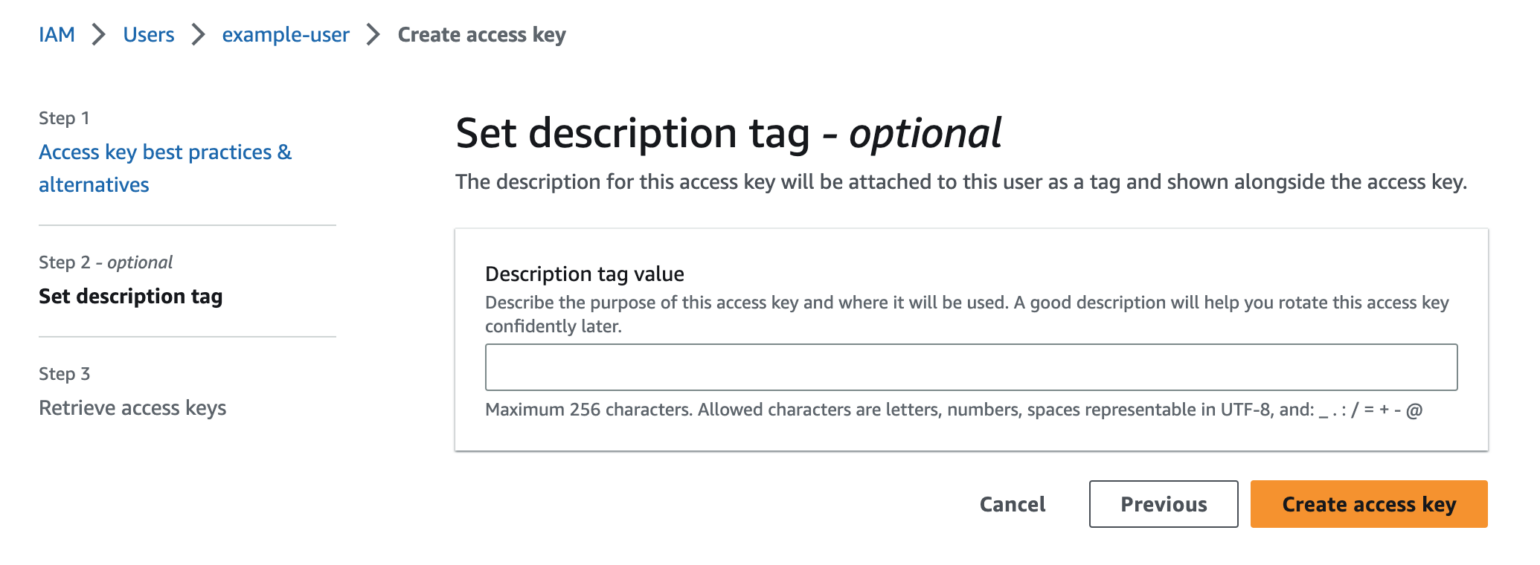
You will be shown the security credentials for the user, which consist of an Access Key ID and a Secret Access Key. Amazon will not show these again so please download them as a .csv and also copy them somewhere safe. If you lose them, you can always create a new set of keys from the console but you cannot retrieve the secret key again later.
Clicking the Done button will return you to the user details page.
Create Bucket
Create the bucket on which you wish to store all your site backups created by Dollie on the create Create bucket page

Define Your Dollie Backup Settings
Now that you have your AWS Access Keys, and your bucket is created, you need to add them to your backup settings so you can use them to work with the Amazon S3 service. In the region field specify the id of the AWS region on which you created your bucket (e.g. eu-west-3)
For AWS the endpoint URL is https://s3.REGIONID.amazonaws.com for example https://s3.eu-west-3.amazonaws.com.
Visit your Dollie Backup Settings in Dollie .
Now put in your bucket settings in the settings field. You can use "Verify Connection" button to test if your settings are correct.

Once your settings are correct visit the Site Dashboard of any of your connected sites, go to Backups and try making a backup. After the initial backup has been created, shortly after you should see the Backup status to be updated to "Remote". Finally check your Storage Bucket in AWS and see if the backup files are present. On the AWS console you should see something like the following:

